RockYou2024
In 2021, a user on RaidForums named "kys234" compiled a bunch of existing wordlists and plaintext passwords from other breaches and combo lists into a single wordlist named "RockYou2021." The wordlist is approximately 92GB when decompressed, containing about 82 billion passwords.
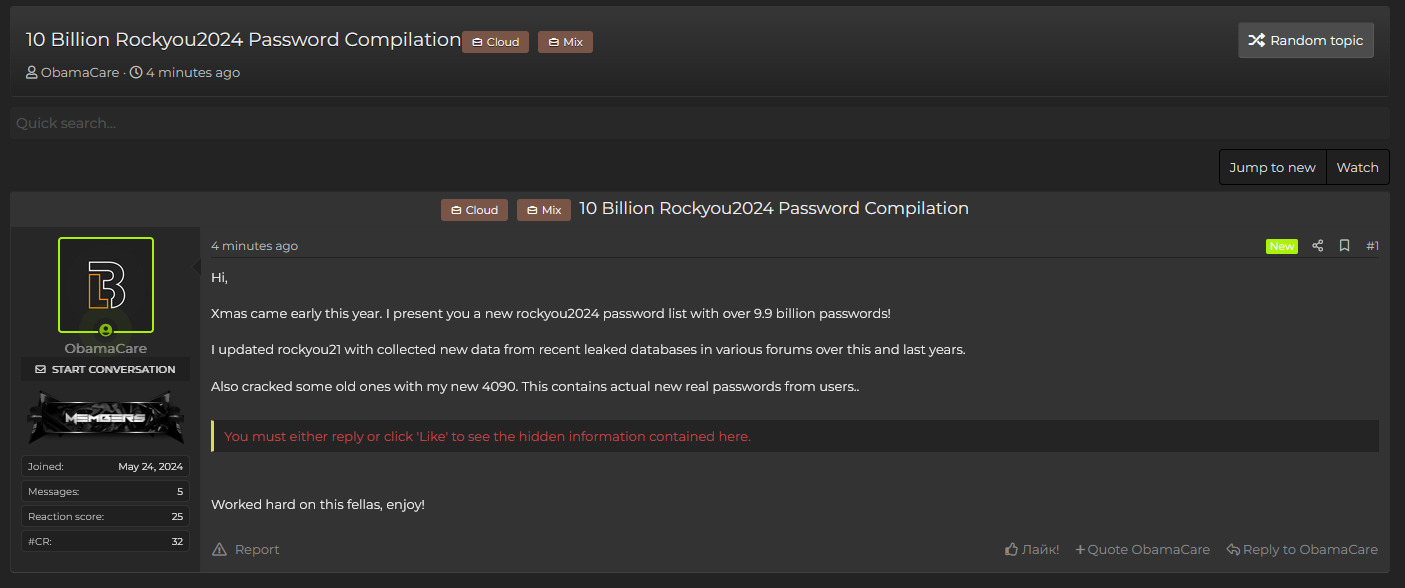
Now in 2024, a user on LeakBase named "ObamaCare" took rockyou2021, added some more passwords from other leaks on top of it to create a new wordlist boasting over 9.9 billion passwords, and shared it as "RockYou2024." The file is around 155GB when decompressed.
Picture from cybernews.com 1
Despite these wordlists consisting only of already-available password combinations, 'tech journalists' rushed to their computers to talk about how the "biggest password leak ever" could "give hackers a huge upper hand." 2
These pieces not only misrepresent RockYou2024 as a "leak," implying a particular service was hacked and a wild amount of passwords from it were dumped, but they also tend to not even mention what RockYou even is: a wordlist from a company that was hacked in 2009 and had 15 million passwords leaked in plaintext; the fact all passwords were plaintext and consisted of real passwords that people were using made it very useful for cracking password hashes.
This is a really interesting event in hacking history, and yet its impact on password security is being overshadowed by (usually bigoted) attention-seeking assholes on forums using its name to have dickmeasuring contests over who can combine the most text files to create the biggest text file.
Nowdays, rockyou.txt has become a bit less relevant. While it's still effective for cracking very weak passwords, modern websites with proper security will disallow extremely weak password combinations, meaning it's getting less likely that a rockyou.txt password will actually be used. Wordlists like Crackstation in conjunction with rules such as dive or OneRuleToRuleThemAll can produce better results. There are also tools like cupp that allow for creating wordlists specifically tailored to information that has been gathered about a target, such as their birthday, favorite bands, pet's names etc.
Furthermore, these solutions don't tend to eat up a ton of hard drive space or waste time checking the hashes for nonsensical password combinations consisting only of a bunch of symbols. No one is going to use something like &&*&&!!!@!!@!@@-@@ as their password, so there's no point in checking it.
See, that's the big issue with these massive wordlists. They're so large and cumbersome, and filled with garbage data, that they don't serve much purpose in an actual scenario where you might try cracking an administrator's password hash or something. Chances are the only people who find this "useful" are the people who will crack half a billion logins so they can beg people on BreachForums to give them 8 credits for the potfile.
So no. This isn't a "digital heist" or "unprecedented leak". 3
This is nothing remotely worth being alarmed about. If your password is in RockYou2024, it's already been leaked long before its release.
Just keep practicing proper security as you should have already been doing. Use a password manager like Bitwarden or KeepassXC to generate and store unique, long and complex passwords for your logins, and use TOTP 2FA wherever possible.
Footnotes
"RockYou2024: 10 billion passwords leaked in the largest compilation of all time", Vilius Petkauskas - Cybernews [link]↩
"This is likely the biggest password leak ever: nearly 10 billion credentials exposed", Matt Binder - Mashable. [link]↩
"Massive password leak alert! RockYou2024 exposes nearly 10 Billion passwords", Geek Staff - AbsoluteGeeks. [link]↩